Since you are on my side, you are
- either in love with me or you are
- looking for information regarding cyber security,
which - taking into account that I can probably rule out point 1 - leads me to believe that there is no need to tell you much about cyber security and the new threats occuring.
If I'm wrong: Regarding point 1, let me know and about point 2 please check following page:
As described on the "Let's talk about Cyber Security" page, the existing management systems (within an organization) must adapt to the changing environment.
We need end-to-end security management along the value chain, which ensures basic protection throughout the company and determines further activities based on risk.
In addition, we need integraded management concepts, which share a central control datbase on " topics", thus, one new requirement of the control framework is, that the responsible manager must integrate the controls that the standard / best practice - that he has decided on - requires need to be integrated in a central "corporate control database".
This aligned and business-driven management system is our "tool" ("figuratively spoken") to master the challenge given.
We have to react to the new threats and master our tool as safely as ABC!
Hence my suggestion to simply call it the "ABC Framework"
|
a ligned b usiness-oriented c ontrol framework |
So, the most difficult thing about bring up a child would be done … a name has been found and now the baby needs to learn walking until it runs by itself and can support in daily business.
Don`t be afraid.
Notably last point is essential easier to archiev with a management system then with kids.
This umpirage could - at least for me - also be due to the fact that I raised significantly more management systems than children, and there are already many frameworks that have been tried and tested in practice for the introduction of such systems.
Anyone who knows me better knows that I don't like to take things over without reflection and that it is difficult for me to come to terms with systems that one tries to impose on me, whether it fits or not.
For this reason I have created a new framework for myself - based on already existing control frameworks - and improved it successively, as I hope.
The improvement is justified by the fact that the aspects of information security and their enablers, such as IT, OT security etc. can be clustered more effectively in domains, as you can see in the following figure.
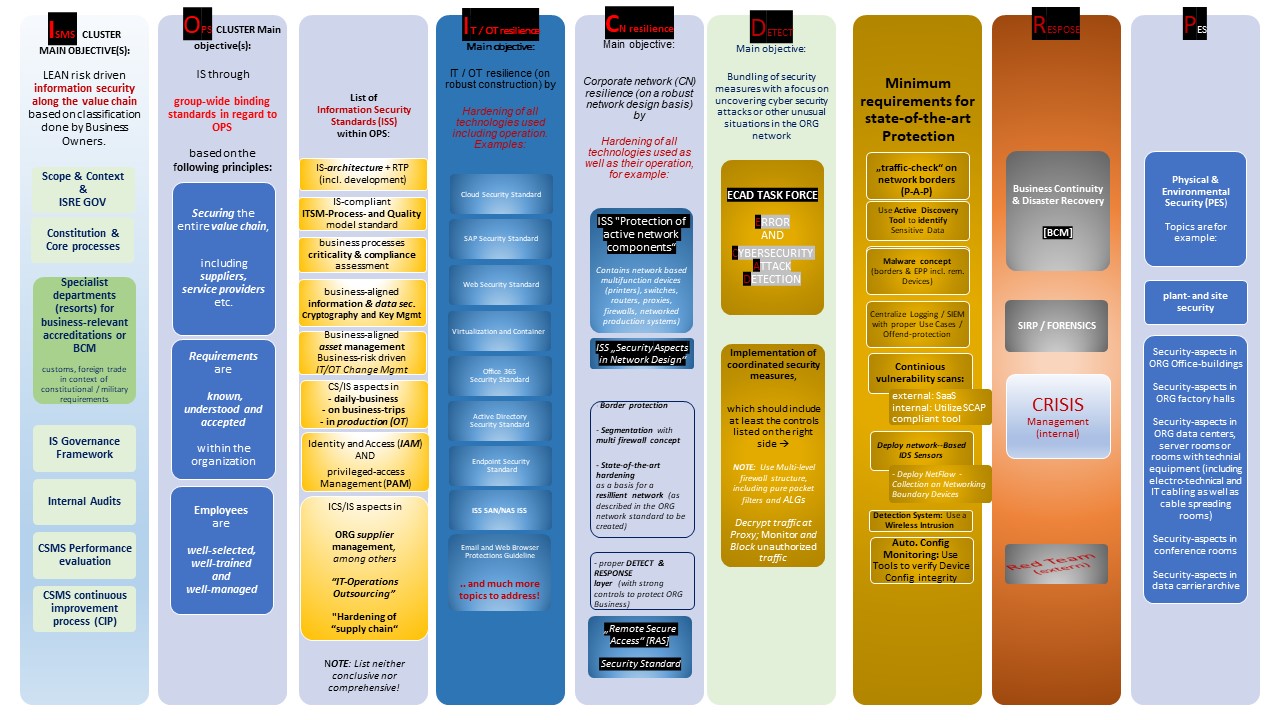
ABC is an organization-wide cyber security framework based on an governance and management approach, thus, ABC is not limited to an organization's IT department, but it certainly includes it.
The framework therefore differentiates between "liable" "c-level" and managers, which are in charge to governn their respective management-topic.
The "c-level" (governance) contains the Stakeholder management (including with regard to agreed corporate goals), which - under addional consideration of risks and chances - leads in the organisational stategy, which is communicated via directional guidelines (principles) within the organisation.
The direction published has to be adjusted by the management (responsible persons in their relevant tasks) by means of a target cascade, e.g. information security control objectives derived from the strategy.
The management, for example CISO, plans (for their relevant area), proper controls in accordance with the given requirements by "C"-Level in order to achieve the striven result (corporate objectives) through appropriate controls.
For example: In the context of information security, an information security manager is usually responsible for setting up an ISMS. Performance and compliance with the implemented management systems are monitored based on agreed specifications and goals, for example through an annual management review as well via the performance management system to be implemented.
One special approach of the control framework, as already said, is that the responsible manager must integrate the controls that the standard / best practice - that he has decided on - requires need to be integrated in the "corporate control database".
In most organizations, the responsible managers of an management system maintains their own controls.
Due to the harmonized structure of all management systems (according to Annex SL) as well as often overlapping subject topics, also rules overlap, for example data protection bins in the DSMS and ISMS, classification of information in almost all systems, etc.
While in the first example the facility management is at most annoyed due to the constant inquiries (""right hand doesn't know what the left is doing"), in the second example there is even the threat that there are different evaluations and thus inconsistencies in the asset directory.
The main advantage of a centralized control database, however, is that you can - with the help of public available mapping tables and on the basis of your own good database - at the push of a button, check and at best confirm compliance with standards that you have never heard before, for eyample Chinese cyber law. Please consider, we actually almost all want the same thing =) but use different words, which sometimes makes it more complicated than necessary. Maybe we should think about a male-female communication mapping !? Well .. maybe after the project.
So, lets come to the nitty gritty: You may be wondering where to find information about the framework.
Anyway, I'll tell you, whether you want it or not: Parts of the framework will be released in Q1/2023 on
http://www.abc-framework.com
#stay tuned